RFID technology has been a revolution in inventory management, access control, and logistics tracking of services. However, despite the ubiquity of technology, it presents itself as an enigma to those unfamiliar with RFID technology.
In this blog post, we will take you on a five-step journey to unravel how RFID works. By the end of this post, you will be able to understand how this technology works simply and clearly.
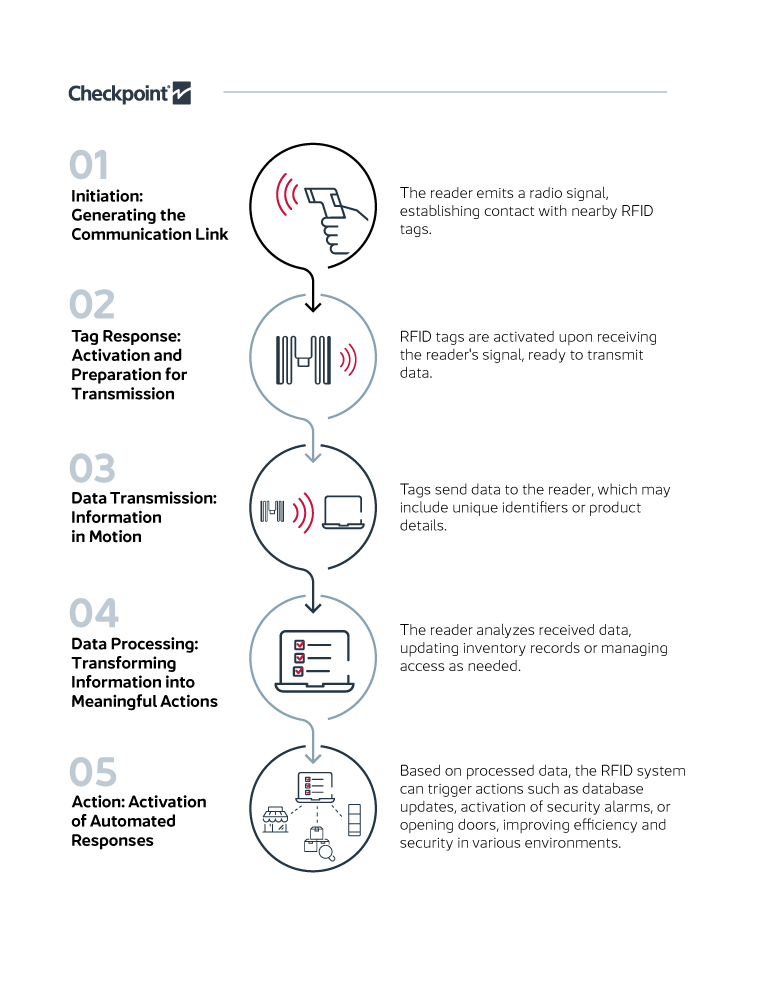
1. Start: Generating the communication link
The first step in understanding what is RFID and how it works is the creation of the communication link between the reader and the tags. This moment is critical in that it allows the basis for data transmission to be established. When the reader emits a radio signal in a specific frequency range, it is actively seeking to establish contact with nearby RFID tags.
The radio signal emitted by the reader acts as a call to the tags within range, inviting them to respond. This process is similar to how a radio antenna tunes to a specific station: it broadcasts a signal on a specific frequency and waits for a response. In this case, the RFID tags that receive the reader's signal prepare to respond, thus initiating the communication process.
2. Tag Response: Activation and Preparation for Transmission
In the second step of the process, the tags respond upon receiving the signal from the RFID reader, activating themselves for data transmission. Passive tags harness the energy provided by the reader's signal to activate, while active tags have their own power source, enabling them to always be ready to respond.
Once activated, the tags are ready to transmit the stored data, which may include unique identifiers or relevant product information. This activation and preparation are crucial to facilitate communication between the tags and the reader, thus paving the way for the next phase of the process.
3. Data Transmission: Information in Motion
After being activated, RFID tags enter the data transmission stage, sending the stored information back to the reader. This phase is crucial for data transfer between the tags and the reader system. The transmitted information can vary, ranging from unique identifiers enabling precise object or asset identification to specific product details such as manufacturing dates, serial numbers, or logistical information.
The versatility of the data allows for its application in various contexts and sectors, from inventory tracking to supply chain management and beyond.
4. Data Processing: Transforming Information into Meaningful Actions
In the fourth step, the RFID reader receives the data transmitted by the tags, and the data processing stage comes into play. In this process, the reader analyzes and organizes the received information to convert it into meaningful and useful actions. Depending on the specific application, this data can be used for a variety of purposes, such as updating inventory quickly and effectively, managing access in security systems, or enhancing the omnichannel experience.
Data processing is essential for maximizing the potential of RFID technology, enabling informed decision-making and process automation.
5. Action: Activation of Automated Responses
Based on the processed data, the RFID system can trigger specific actions such as updating databases, activating security alarms, or opening doors.
Among the possible actions are database updates, where the collected information is integrated into inventory records or asset management systems to maintain accurate real-time tracking. Additionally, the RFID system can activate security alarms upon detecting anomalies or unauthorized products or trigger the opening or closing of doors or restricted access points, allowing or denying entry based on the authorization of detected RFID tags. These automated actions not only streamline processes but also enhance efficiency and security across a variety of environments, from warehouses and distribution centers to industrial and commercial facilities.
In conclusion, RFID technology has made a significant impact on inventory management, access control, and logistical tracking across various services. Despite its widespread use, its operation may remain mysterious to those unfamiliar with it. In this blog post, we've embarked on an educational journey of five steps to unravel the workings of RFID.
